- Share
- Share on Facebook
- Share on X
- Share on LinkedIn
Explore our research demos in softwares vulnerabilities
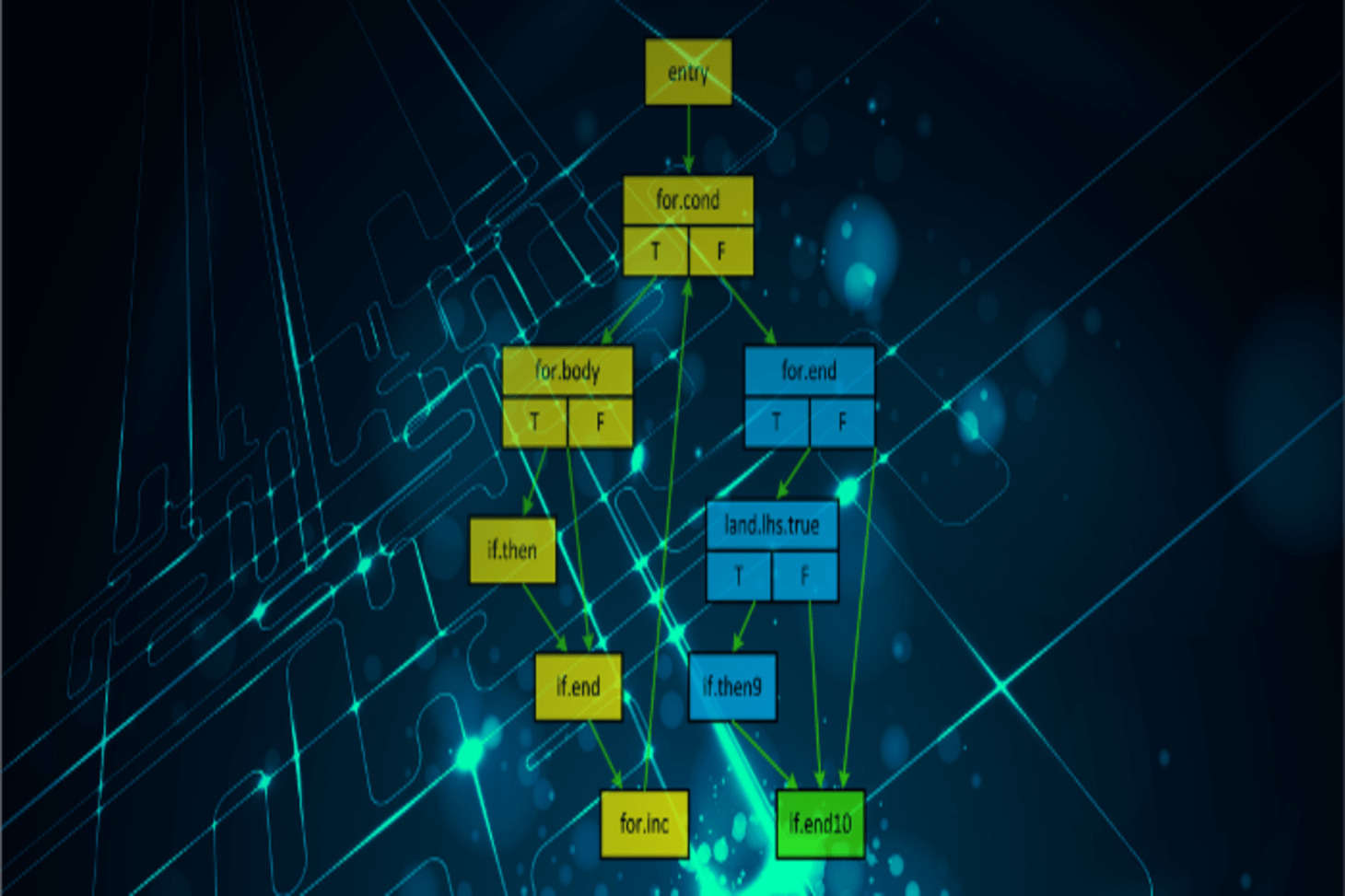
LAZART
LAZART is a tool based on concolic execution that evaluates the robustness of LLVM code against multi- fault attacks.
To explore more about LAZART and its capabilities, please follow the link : LAZART
FISSC : Fault Injection & Stimulation Secure Collection
FISSC is a collection of C codes with countermeasures against fault injections associated to attack scenarios.
To learn more about FISCC and explore its capabilities, please follow the link: FISSC
BISM : Bytecode Instrumentation for Software Monitoring
BISM is a bytecode-level instrumentation tool for Java-bytecode based language that features an expressive yet high-level control-flow-aware instrumentation API. BISM can be used for static and dynamic analysis of programs.
In particular, BISM was used to instrument programs to detect test inversion and arbitrary jump attacks.
To explore more about BISM and download it, please follow the link: BISM : Bytecode Instrumentation for Software Monitoring
CLAM : Cross-Layer Fault Analysis for Microprocessor Architectures
The CLAM project aims at securing the software components (e.g., microprocessors and microcontrollers) intended for the IoT market, as well as for critical Cyber Physical Systems.
It requires, on the one hand, analyzing their vulnerabilities and, on the other hand, defining hardware and software countermeasures at the most appropriate cost.
To access the demonstration and detailed information, follow the link: CLAM
For a comprehensive list of our publications on the subject, please refer to this link.
- Share
- Share on Facebook
- Share on X
- Share on LinkedIn